[Next] [Up]
[Previous] [Index]
Quadibloc 2002E: The Main Combiner for the Core Rounds
The combiner used to apply the 128-bit f-function output uses elements that will be familiar
from Quadibloc XI and Quadibloc 2002. In addition to using a structure of the "Fractal
Feistel" type, note the swap halves operations in the middle of the overall combiner and in
the middle of the two combiners within the round. This is done so that the structure can be
self-inverse. In order to avoid the need to modify the algorithm slightly for decipherment,
in two places a bit swap is introduced into the cryptographic core rounds.
The final part of the 128-bit f-function is also shown in this diagram; it includes the
bijective key-dependent S-box S16, and an ICE-style swap operation. This operation allows the
inverse of the cipher to be produced without changing the algorithm; instead, in addition to reversing
the order of subkeys EK13 through EK20, these keys are also subjected to a one's complement operation,
after they go through the 4 of 8 code, to prepare the deciphering keys.
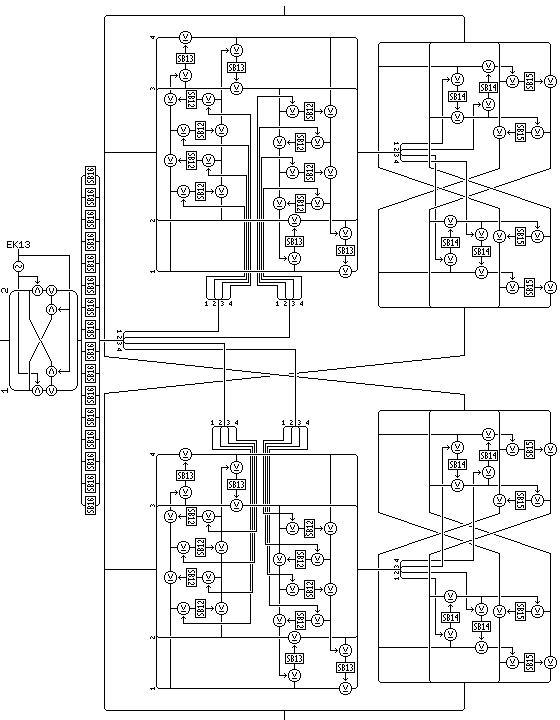
The first operations shown in the diagram above constitute the final part of the
overall f-function for a cryptographic core round, and they consist of a bit swap followed
by byte substitution.
First, a 64-bit exchange key is applied to the 128-bit output of the
preceding portions of the f-function for the round, being
considered as divided into two 64-bit halves; where a bit in the exchange
key is a zero, corresponding bits in the two halves are unaffected;
where a bit in the exchange key is a one, corresponding bits in the two
halves are switched.
Then, the 128-bit value is considered as being composed of sixteen bytes,
and each byte is replaced by its substitute in key-dependent S-box SB16.
The combiner proper consists of two rounds with a swap of 32-bit halves of the
64-bit half block being affected in between.
Each round uses the combiner found in Quadibloc 2002 as its f-function,
and then the similar combiner used in Quadibloc XI, modified by having a
swap halves operation in the middle to make it symmetric (as well as
having the order of byte use in the second round reversed), as its combiner,
thus applying the input to the right half of the overall 128-bit block
in a highly nonlinear fashion.
The f-function within the first round of the combiner proceeds as
follows:
- First, four Feistel rounds are performed to serve as an f-function,
enciphering a copy of the first two bytes of the right half of the block
to produce a 16-bit value to be used as a pair of subkeys to later modify
a copy of the last two bytes
of the left 32-byte half of the right half of the block, as part of the
procedure for producing the four byte output of the original combiner
f-function as follows:
- A second copy of bytes 1 and 2 of the right half of the block is made, from
the copies of bytes 1 through 4 of the right half of the block which were used
as the input to the f-function.
- Byte 1 of the 128-bit round f-function output
is XORed with the second copy of byte 1 of the right half of the block
to produce a value used to index into key-dependent S-box SB12, without
the second copy of byte 1 being changed for subsequent use.
- The value selected from S-box SB12 is then XORed with the second copy of
byte 2 of the right half of the block, changing the second copy (but not the first copy).
- Byte 2 of the 128-bit f-function output is XORed with the copy of
byte 2 of the right half of the block
as modified. The result of this XOR is used as an index into key-dependent
S-box SB12, while the copy of byte 2 of the right
half of the block is not changed for
subsequent use.
- The byte found in S-box SB12 in the previous step is XORed with the
second copy of byte 1 of the right half of the block, changing the second copy
(but not the first copy).
- Byte 3 of the 128-bit f-function output is XORed with the second
copy of byte 1 of the right half of the block
as modified. The result of this XOR is used as an index into key-dependent
S-box SB12, while the second copy of byte 1 of the right half of the block is not changed for
subsequent use.
- The value selected from S-box SB12 is then XORed with the second copy of
byte 2 of the right half of the block as modified.
- Byte 4 of the 128-bit f-function output is XORed with the second copy of
byte 2 of the right half of the block
as modified. The result of this XOR is used as an index into key-dependent
S-box SB12, while the second copy of byte 2 of the right half of the block is not changed for
subsequent use.
- The byte found in S-box SB12 in the previous step is XORed with the second
copy of byte 1 of the right half of the block as modified.
- Then, the output of the f-function, the modified second copy of bytes 1 and
2 of the right half of the block, is applied to the original copies of bytes 3 and 4
of the right half of the block, modifying them for use as part of the output of the
32-bit wide f-function that forms part of the combiner, as follows:
- The XOR of byte 3 of the right half of the block and the modified second copy of byte 1 of
the subblock are used to index into key-dependent S-box SB13. Byte 3 of the first copy
of the right half of the block is not altered by this step.
- The byte found in S-box SB13 is XORed with byte 4 of the original copy of the right
half of the block, modifying it for use as part of the output of the
32-bit wide f-function that forms part of the combiner.
- The XOR of the original copy of byte 4 of the right half
of the block as modified, and the modified second copy
of byte 2 of the right half of the block are used to index into S-box SB13. Byte 4 of the
original copy of the right half of the block is not altered by this step.
- The byte found in S-box SB13 in the preceding step is XORed with byte 3
of the original copy of the right
half of the block, modifying it for use as part of the output of the
32-bit wide f-function that forms part of the combiner.
In the second round, bytes 3, 4, 1 and 2 of the original copy of the right half
of the block, as currently modified in the case of bytes 3 and 4,
serve the same functions as
bytes 1, 2, 3, and 4 respectively did in the first round, and bytes 5, 6, 7, and 8
of the 128-bit f-function output perform the same function as bytes 1, 2, 3, and 4
of the 128-bit f-function output performed in the first round. The rounds
are performed in place, so there is no interchange of bytes to move them
into the positions of the bytes whose roles they now perform.
As this combiner serves as an f-function, its 32 bit output is now used to modify
the right half of the right half of the original 128-bit block; this is a permanent
modification which actually changes bits on their way from plaintext to ciphertext.
This modification is performed by means of a combiner very similar to the combiner
just described, except that it has only two Feistel rounds in its innermost level where
the other one had four, as it has only 32-bits of input with which to modify a 32-bit
value.
The first round proceeds as follows:
- First, two Feistel rounds are performed to serve as an f-function,
enciphering a copy of the first two bytes of the subblock to produce a
16-bit value to be used as a subkey to later modify the last two bytes
of the block, as follows:
- A copy of bytes 5 and 6 of the right half of the block is made.
- Byte 1 of the output from the combiner previously described
is XORed with the copy of byte 5 of the right half of the block
to produce a value used to index into key-dependent S-box SB14, without
the copy of byte 5 being changed for subsequent use.
- The value selected from S-box SB14 is then XORed with the copy of
byte 6 of the right half of the block, changing the copy (but not the original).
- Byte 2 of the output from the combiner previously described is XORed with the copy of
byte 6 of the right half of the block
as modified. The result of this XOR is used as an index into key-dependent
S-box SB14, while the copy of byte 6 of the right half of the block is not changed for
subsequent use.
- The byte found in S-box SB14 in the previous step is XORed with the
copy of byte 5 of the right half of the block, changing the copy (but not the original).
- Then, the output of the f-function, the modified copy of bytes 5 and
6 of the right half of the block, is applied to bytes 7 and 8 of the right
half of the block, modifying them
permanently, as follows:
- The XOR of byte 7 of the right half of the block and the modified copy of byte 5 of
the right half of the block are used to index into S-box SB15. Byte 7 of the right
half of the block is not altered by this step.
- The byte found in S-box SB15 is XORed with byte 8 of the right half of the block,
permanently modifying it.
- The XOR of byte 8 of the right half of the block as modified, and the modified copy
of byte 2 of the right half of the block which is also byte 2 of the previously described
f-function output are used to index into S-box SB15. Byte 8 of the
right half of the block is not altered by this step.
- The byte found in S-box SB15 in the preceding step is XORed with byte 7
of the right half of the block, permanently modifying it.
Then, the two halves of the right half of the right half of the block are swapped; thus,
bytes 5 to 8 of the right half of the block are shifted from the order
5 6 7 8
to the order
7 8 5 6
In the round which forms the second half of the combiner, the new bytes 5 and 6, formerly
bytes 7 and 8, of the left half of the block, are processed as before to form an f-function
output. The third and fourth bytes of the previous f-function output are used for this,
in place of the first and second bytes of the previous f-function output respectively.
Subsequently, however, the modified copy of byte 6 is XORed with byte 8 to form the
index into SB15 which locates the entry that is used to XOR with byte 7, permanently modifying it, first; then,
after that is done, the modified copy of byte 5 is XORed with byte 7 to form the index into
SB15 which locates the entry that is used to XOR with byte 8, permanently modifying it.
This reversal makes the f-function symmetrical, and is easier to understand from the
diagram above than from a written description.
Then, halves of the entire 64-bit right half of the block are swapped, changing the
order of bytes from
1 2 3 4 5 6 7 8
to
5 6 7 8 1 2 3 4
and then, using the new bytes 1 through 8 of the right half of the block, first the
combiner with an inner four-round part is performed again, using bytes 9 through 16
of the 128-bit f-function output in place of bytes 1 through 8 of the 128-bit f-function
output, respectively, and then bytes 5 through 8 of the right half of the block are
actually modified using the same combiner as before, except that now byte 4 of the previous
f-function output is used where byte 1 of that output was used before, then byte 3 instead of
byte 2, byte 2 instead of byte 3, and byte 4 instead of byte 1.
[Next] [Up]
[Previous] [Index]
Next
Start of Section
Skip to Next Chapter
Table of Contents
Main Page

