Although originally invented much earlier, by Thomas Jefferson, this type of cipher machine became generally known after its later re-invention by Commandant Etienne Bazeries, who wrote a book about cryptology which recommended this device.
About 20 or 30 disks, each with a different scrambled alphabet on the edge, and with a hole in the centre so they can all be stacked on a common axle, make up the device. The disks can be numbered on one side, and the order in which they are stacked can be used as a key that can easily be changed.
To encipher a message, rotate the disks so that its letters line up in one row, and take the letters in any other row as the encrypted message. Decipherment is possible, because it is easy to pick out one row of plaintext among 24 others of gibberish that are possible.
This is quite a secure cipher device, especially considering that it doesn't involve a lot of fancy technology. Since every letter in a block is displaced through a different alphabet, and every block has a different displacement, it is even possible to mistakenly assume that it is unbreakable.
However, it isn't unbreakable. Like the Enigma, which we will meet later, no letter can represent itself. This allows probable plaintext to be positioned against intercepted messages.
The main attack against this type of cipher is the de Viaris method. If the alphabets on the cylinder are poorly chosen, it may be that the fifth letter clockwise from E, for example, can never be some letters, and is one particular letter several times. Thus, an opponent who has a copy of the cylinder itself and some plaintext may be able to identify the displacement for a block - and, with that, then determine the order of the disks.
The alphabets on the M-94, a version of the Bazeries cylinder made from aluminum, and used by the U.S. during the Second World War, were chosen to be part of a Latin square to be more resistant to a de Viaris attack. A Latin square is an N by N square containing the numbers from 1 to N, each N times, so that no number occurs twice in either the same row or the same column. For example,
1 2 3 4 5 3 1 4 5 2 2 5 1 3 4 5 4 2 1 3 4 3 5 2 1
is an example of a Latin square. However, since
1 2 3 4 5 2 3 4 5 1 3 4 5 1 2 4 5 1 2 3 5 1 2 3 4
is also a Latin square, and is obviously not a good type of sequence for a cylinder cipher, as every cylinder has the same alphabet, only shifted by one, there is more to choosing a good set of alphabets for a cylinder than simply using a Latin square.
Ideally, if one were using 25 cylinders for a 26-character alphabet, one would like a sequence such that, if one aligns any one letter to form a solid row of that letter, then the remaining 25 letters on the 25 cylinders are, in each case, a Latin square. Then, for each displacement, and each letter, all substitutes would be equally possible. I do not know whether or not it is possible to fulfill this condition.
Even when the de Viaris attack is not possible, cylinder ciphers can be broken. During World War II, the U.S. used an improved version of the cylinder cipher. Strips instead of disks were used (which, of course, makes no difference in itself), and there were 100 of them to choose from. The cipher procedure involved choosing 30 strips, but breaking up the message into blocks of only 15 letters long.
Despite all this, and the fact that they did not have a captured specimen of the device to work with, cryptanalysts in Nazi Germany were able to break messages enciphered with the M-138-A.
If one does not have a copy of the device, and in any case the strips or disks used have been made resistant to the de Viaris attack, it is still possible to attack a Bazeries cylinder if one has several hundred messages, all sent with the same key.
Using the kappa test (the fact that two unrelated plaintexts will have more identical characters in corresponding positions than two sequences of random letters, which will have one coincidence for every 26 letters), one can group together messages with the same displacement from the row with the plaintext message.
Once this is done, and if one had enough messages to work with, frequency counts can be used for each position.
After the war, a further improvement was made to the strip cipher. In addition to a daily order for the strips, keylists also gave a table with a column number (or a blank) under each of the 26 letters. A random set of five letters was chosen for each message; the column numbers in the frame corresponding to these letters were not used to encipher that message. These were called "Channel Elimination Numbers", and the numbers where the numbers of positions in the frame, not strips. (Since which strip went in which column was also part of the same daily key, this was important operationally - for ease of sending different messages, each with its own indicator, during the one day, not cryptographically.)
As this essentially varied the key for every message, it prevented the statistical attack outlined above.
The Bazeries cylinder relies on the input plaintext being plaintext, with some redundancy, so that it can be found. Of course, if one allows expanding the text with an extra letter, or using a pre-arranged scheme to pick the ciphertext row, variations of the cipher method can be designed without this limitation, and therefore useful for the subsequent encipherment of ciphertext.
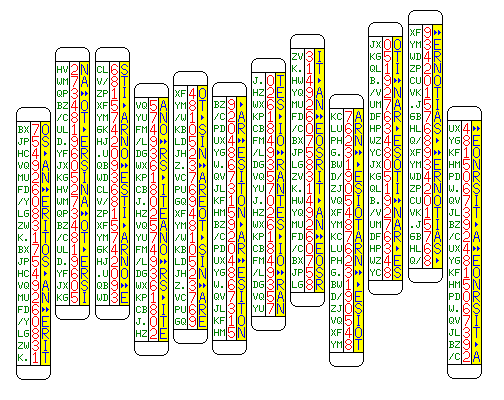
The following diagram, showing a different kind of strip used for this type of encipherment:

retains the limitation, while reducing it somewhat. The plaintext SEND MONEY is being enciphered to the numerical ciphertext 345589628759, and its redundancy is being reduced in the process by the same amount as a straddling checkerboard would do so.
The principle involved is that a plaintext letter, if found on the right side of the strip, is represented by that single strip; otherwise, two strips, the first with the symbol > or >> on the right-hand side, and the second with the plaintext letter in the first, or second, column on the left-hand side are aligned to represent that letter.
Such a method, though, is only practical if, at least with practice, the row containing plaintext "leaps out" at the eye of the decipherer.
In the diagram above, the first row contains the nonsense string OGOSRIERH, while the second one contains the desired plaintext SENDMONEY, and the third contains YORNEPCF, but that does seem to take some effort to see.
Next
Chapter Start
Skip to Next Section
Table of Contents
Main Page