SAFER+ is the proposal of Cylink Corporation for the Advanced Encryption Standard, and its description is available at http://www.cylink.com/internet/library.nsf/pages/SAFER/. It is very similar to the original 64-bit block cipher SAFER.
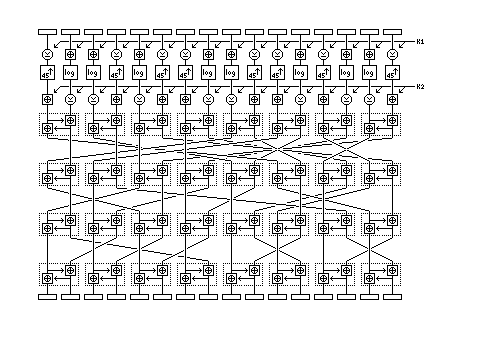
The following diagram shows one round of SAFER+:

it uses the same S-boxes as SAFER in the same way. Instead of the regular "butterfly" formation of Pseudo-Hadamard Transforms used in the original SAFER, a slightly irregular arrangement is used, so that the net result of the operations, given in the document as the matrix M (it stated that that matrix could be realized by a four-layer PHT network similar to the three-layer one in SAFER, but did not give the network; thus this diagram rectifies the omission) has certain desirable properties.
One other improvement in SAFER+ over SAFER is that after matrix M is applied in the last round, one extra subkey is applied to the block, using the same sequence of alternating XORs and additions as is used for the first subkey in a round. This means that the final application of matrix M is not a waste of time in terms of cryptographic security.
For a key length of 128 bits, 8 rounds are used; for 192 bits, 12 rounds; and for a 256-bit key, SAFER+ has 16 rounds.
The key schedule of SAFER+ is quite simple. The key, whatever its length, has one byte appended to it, equal to the XOR of all the bytes in the key.
The first subkey consists of the first 16 bytes of the key. For each remaining subkey, first rotate the expanded key left 11 bits, then take the first 16 bytes of the result, and use them after XORing them with a constant. I am not reproducing the constants here; the paper describing SAFER+ gives them, but in decimal form.