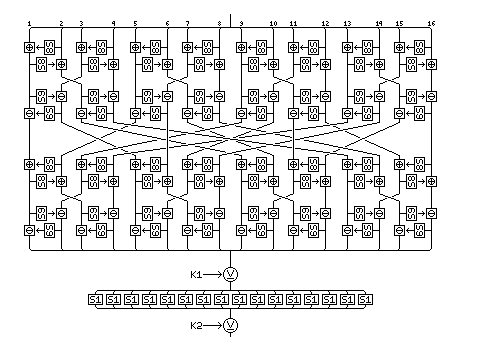
Quadibloc 2002A is a block cipher with a structure inspired by those of Rijndael and SAFER, and with a 128-bit block.
This diagram illustrates the basic round of Quadibloc 2002A:

A round consists of four phases, the diffusion phase, the first key phase, the nonlinearity phase, and the second key phase.
The two key phases consist merely of XORing the current value of the block with a 128-bit subkey.
The nonlinearity phase consists simply of replacing each byte of the block with its corresponding entry in S-box S1. For this cipher, S-box S1 is the self-inverse S-box created by taking the S-box called S1 derived from Euler's constant, as used in other ciphers of the Quadibloc series, and taking as the equivalent of each element in it the element in that S-box reversed. That is, as the original S-box begins and ends:
147 196 164 55 ... 63 149 110 23
the S-box S1 used in this cipher will have, among its contents:
23) 147 55) 63 63) 55 110) 196 147) 23 149) 164 164) 149 196) 110
In full, the S-box S1 used with this cipher is:
232 116 188 183 118 218 184 40 137 185 157 230 200 130 31 100 140 178 126 206 237 222 220 147 70 36 53 254 111 210 204 14 78 255 71 76 25 84 64 239 7 180 60 75 169 217 225 82 203 73 141 94 109 26 182 63 181 103 158 145 42 142 97 55 38 159 201 186 80 151 24 34 173 49 129 43 35 252 32 150 68 171 47 248 37 221 238 101 127 153 155 162 134 253 51 120 107 62 131 233 15 87 161 57 174 170 240 96 243 52 196 28 235 216 231 122 1 195 4 128 95 245 115 152 125 124 18 88 119 74 13 98 191 242 92 229 138 8 136 172 16 50 61 241 214 59 198 23 228 164 79 69 123 89 175 90 234 10 58 65 227 102 91 211 149 179 213 246 197 44 105 81 139 72 104 154 207 189 17 165 41 56 54 3 6 9 67 215 2 177 193 132 223 190 199 117 110 168 146 194 12 66 209 48 30 251 19 176 224 202 29 163 244 166 144 187 113 45 5 247 22 85 21 192 208 46 250 160 148 135 11 114 0 99 156 112 249 20 86 39 106 143 133 108 212 121 167 219 83 236 226 205 77 93 27 33
The diffusion phase, unlike the corresponding structure in most ciphers of this type, is both keyed and nonlinear. It uses the key-dependent S-boxes S8 and S9, in a structure designed so that reversing the roles of the two S-boxes creates the inverse of the diffusion phase.
In the diffusion phase, the block is divided into pairs of bytes. In each pair, first the byte on the left has the element of S8 the byte on the right points to added to it modulo 256, and then the byte on the right has the element of S8 the byte on the left points to added to it modulo 256. In the absence of S8, this would essentially be a pseudo-Hadamard transform, as used in SAFER.
The bytes are next considered as belonging to groups of four, and the middle two bytes of each such group are swapped.
Then, considered as pairs of bytes again, first the byte on the right has the element of S8 the byte on the left points to subtracted from it modulo 256, and then the byte on the left has the element of S8 the byte on the right points to subtracted from it modulo 256. In the absence of S9, this would essentially be the inverse of the pseudo-Hadamard transform.
Since at this point, we have four groups of four bytes, each thoroughly mixed within itself, a byte transpose is performed, transposing the sixteen bytes of the block from the order
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
to the order
1 5 9 13 2 6 10 14 3 7 11 15 4 8 12 16
and thus placing one byte from each group of four into each new group of four.
Then the use of S8 in a pseudo-Hadamard transform and the use of S9 in an inverse pseudo-Hadamard transform is repeated.
If S8 and S9 were replaced by the identity transformation, the operation performed by the diffusion phase would be matrix multiplication modulo 256 with the following matrix:
+4 -2 +4 -2 -2 +1 -2 +1 +4 -2 +4 -2 -2 +1 -2 +1 +4 -2 +4 -2 -2 +1 -2 +1 +8 -4 +8 -4 -4 +2 -4 +2 -2 +1 -2 +1 +2 -1 +2 -1 -2 +1 -2 +1 +2 -1 +2 -1 -2 +1 -2 +1 +2 -1 +2 -1 -4 +2 -4 +2 +4 -2 +4 -2 +4 -2 +8 -4 -2 +1 -4 +2 +4 -2 +8 -4 -2 +1 -4 +2 +4 -2 +8 -4 -2 +1 -4 +2 +8 -4 +16 -8 -4 +2 -8 +4 -2 +1 -4 +2 +2 -1 +4 -2 -2 +1 -4 +2 +2 -1 +4 -2 -2 +1 -4 +2 +2 -1 +4 -2 -4 +2 -8 +4 +4 -2 +8 -4 -2 +2 -2 +2 +1 -1 +1 -1 -2 +2 -2 +2 +1 -1 +1 -1 -2 +2 -2 +2 +1 -1 +1 -1 -4 +4 -4 +4 +2 -2 +2 -2 +1 -1 +1 -1 -1 +1 -1 +1 +1 -1 +1 -1 -1 +1 -1 +1 +1 -1 +1 -1 -1 +1 -1 +1 +2 -2 +2 -2 -2 +2 -2 +2 -2 +2 -4 +4 +1 -1 +2 -2 -2 +2 -4 +4 +1 -1 +2 -2 -2 +2 -4 +4 +1 -1 +2 -2 -4 +4 -8 +8 +2 -2 +4 -4 +1 -1 +2 -2 -1 +1 -2 +2 +1 -1 +2 -2 -1 +1 -2 +2 +1 -1 +2 -2 -1 +1 -2 +2 +2 -2 +4 -4 -2 +2 -4 +4
which is self-inverse.
Note that the Square attack is possible against a single round of this cipher, due to the structure of the diffusion phase. However, since the pseudo-Hadamard transform does feed back some of the bytes on themselves, it is only for some input bytes running through their 256 possible values that some output bytes will run through their 256 possible values.
The cipher consists of fifteen rounds, followed by one extra diffusion phase, so that there are sixteen diffusion phases in the cipher.
While this cipher certainly could use subkey material and S-boxes S8 and S9 generated by the method used in Quadibloc XI, it is appropriate for a cipher like this which has the potential of being used in circumstances involving minimal hardware to have a simple key schedule.
Subkey material will therefore be generated as follows, from a 128-bit key:
the key will be repeatedly enciphered by one round of the cipher, where S-boxes S8 and S9 shall contain the contents of the S-box S1 used with this cipher, and where the two subkeys applied in the two key phases shall be 0 and 1 the first time, 2 and 3 the second time, and so on, where numbers have their most significant bits on the left.
The 30 subkeys used by this key schedule shall be, in order, the subkeys
K1 K3 K5 K7 K9 K11 K13 K15 K17 K19 K21 K23 K25 K27 K29 K30 K26 K22 K18 K14 K10 K6 K2 K28 K24 K20 K16 K12 K8 K4
thereby avoiding regularity in the key schedule, and possible vulnerability to attacks resembling slide attacks.
Then, S-box S8 will be generated as follows:
Generate 256 bytes of subkey material by generating sixteen 128-bit subkeys.
These 256 bytes, starting with the leftmost byte of the first subkey so produced, are then matched against an array initially containing S1. For an index going from 0 to 256, if the subkey byte at that index has a value different from the index, the bytes in the array at the index and value positions are exchanged.
S-box S9 is generated the same way, except the array is initially loaded with S8.
For a 256-bit key, or a key that is any higher multiple of 128 bits, repeat the process, starting the subkeys from 0 and 1 again, except: XOR the existing subkeys with the material generated, and these subsequent times, do the subkeys in order from K1, K2, K3... to K30, not as was done for the first 128 bits, and then for S8 and S9, start from the former values of each of them to do the swaps to further scramble them.
To decrypt, it is simply necessary to exchange S8 and S9, and use the subkeys applied in the key phases in reverse order.
That the diffusion phase can be made into its own inverse by this operation, if it is not clear, is a consequence of the fact that it has the form:
A B A'inv C A B A'inv
where A is the operation of a pseudo-Hadamard transform with S8, and A' is the operation of a pseudo-Hadamard transform with S9, and thus A'inv is the inverse of that operation, and B is the operation of swapping the two middle bytes of every group of four, which is self-inverse, and C is the operation of doing a matrix transpose on the square formed by the sixteen bytes of the block, also self-inverse.
Next
Start of Section
Skip to Next Chapter
Table of Contents
Main Page