Instead of arbitrarily choosing a list of common words or syllables to give cipher equivalents for, one might be able to achieve the same increased security another way, by enciphering several letters at once using some simple system that handles all possible combinations of two letters, or three letters.
Of course, one could just use a random list of all 676 possible combinations of two letters, and this would give the maximum possible security for a system that handles two letters at a time.
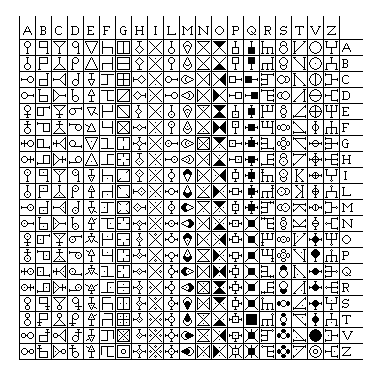
Or, one could even follow the lead of Giovanni Battista della Porta, and use a table giving different symbols for every pair of letters:

This is a redrafting of the table of 400 symbols for the digraphs of a 20-character alphabet given by Porta in his De Furtivis Literatum Notis. In the original, there are a few typographical errors, leading to some duplicate symbols:
ZI is a duplicate of ZO, VM is a duplicate of LL, NG is a duplicate of NB. The replacements for the first two were obvious, that for NG is somewhat arbitrary.
Naturally, since Porta was expressing the idea of a digraphic cipher in print for the first time, he did so in a way that seems unsophisticated by modern standards.
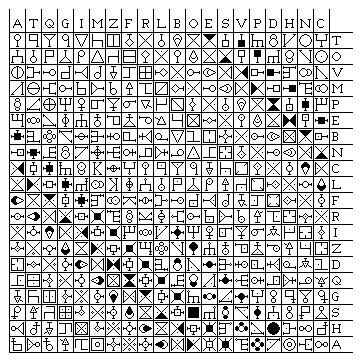
The columns in Porta's diagram all contain characters related in shape. This makes it easier to look up a symbol, but also gives away information. One way to retain the advantage of easily finding a symbol, but without giving away information to the cryptanalyst, is illustrated in the diagram above: have similar symbols arranged along the diagonals of the diagram, and use mixed alphabets along the edges. While a digraphic symbol cipher is something that isn't too practical, similar techniques have been used for small code charts to make them practical and secure.
Systematic methods of enciphering several letters at once, without simply using a very large table, will be outlined in what follows. Fractionation lends itself to many complicated and bizarre developments, a few of which will be illustrated there.
Hopefully, all the examples that will be contained in the following pages will prove a starting point from which you can let your imagination run wild.
Fractionation, although a powerful technique, has seldom been used in paper-and-pencil ciphers, because it is too complicated and prone to error. Two schemes that actually were used, the ADFGX or ADFGVX cipher used by Germany in the First World War, and the VIC cipher used by Reino Hayhanen while engaged in espionage in the United States, involved substituting multiple symbols for each letter, and transposing the letters or digits so obtained, but did not attempt to then reconstitute the symbols back into letters.
Representing letters by five symbols from a set of two, or three symbols from a set of three, has tended to be used mostly for steganography, as proposed by Bacon and Trithemius. (That is, in the former case, if one does not count the use of the 5-level code for teletypewriters.)
The Hagelin B-21 and its relatives also involved fractionation, combined with polyalphabeticity but without transposition.
A Table of Powers, useful in finding ideas or opportunities to perform fractionation.
Next
Chapter Start
Skip to Next Section
Table of Contents
Main page
Home page