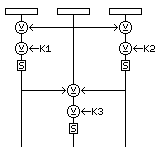
A simple block cipher acting on 24-bit blocks was devised by Dr. Eric E. Johnson for use with the radio communications standard known as MIL-STD-188-141A and FED-STD-1045, using eight rounds of the interesting type shown in the illustration below:

The twenty-four one byte subkeys that constitute its subkey material are produced by XORing together successive repetitions of the seven-byte key with successive repetitions of an eight-byte value giving such information as the time and date of the radio transmission, its frequency, and the number of the encrypted block in the message. Thus, no two blocks are encrypted by the same key, but the keys are linearly related; also, purists will also note that the cipher begins and ends with unkeyed steps. But the cipher was not claimed to be secure for general-purpose use, and its construction is unique and interesting. The block length was doubtless chosen to correspond to the twelve data bits that could be accepted by the Golay code, and this algorithm may also be commended, as 24 bits is about the size of the mantissa of a 32-bit floating-point number, to those seeking to use a cryptographic algorithm to generate pseudorandom numbers of extremely high quality.
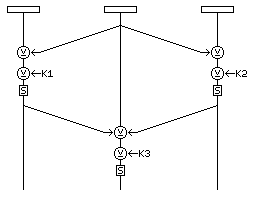
A somewhat more pictorial view of the round, following the lead of the overview diagram in the paper available at the link given above, is shown in the following diagram:
The contents of the S-box which it uses are the following:
156 242 20 193 142 203 178 101 151 122 96 23 146 249 120 65 7 76 103 109 102 74 48 125 83 157 181 188 195 202 241 4 3 236 208 56 176 237 173 196 221 86 66 189 160 222 27 129 85 68 90 228 80 220 67 99 9 92 116 207 14 171 29 61 107 2 93 40 231 198 238 180 217 124 25 62 94 108 214 110 42 19 165 8 185 45 187 162 212 150 57 224 186 215 130 51 13 95 38 22 254 34 175 0 17 200 158 136 139 161 123 135 39 230 199 148 209 91 155 240 159 219 225 141 210 31 106 144 244 24 145 89 1 177 252 52 60 55 71 41 226 100 105 36 10 47 115 113 169 132 140 168 163 59 227 233 88 128 167 211 183 194 28 149 30 77 79 78 251 118 253 153 197 201 232 46 138 223 245 73 243 111 143 229 235 246 37 213 49 192 87 114 170 70 104 11 147 137 131 112 239 164 133 248 15 179 172 16 98 204 97 64 247 250 82 127 255 50 69 32 121 206 234 190 205 21 33 35 216 182 12 63 84 26 191 152 72 58 117 119 43 174 54 218 126 134 53 81 5 18 184 166 154 44 6 75
and its inverse, which must be used when deciphering, is the following:
103 132 65 32 31 248 254 16 83 56 144 195 230 96 60 204 207 104 249 81 2 225 99 11 129 74 233 46 162 62 164 125 219 226 101 227 143 186 98 112 67 139 80 240 253 85 175 145 22 188 217 95 135 246 242 137 35 90 237 153 136 63 75 231 211 15 42 54 49 218 193 138 236 179 21 255 17 165 167 166 52 247 214 24 232 48 41 190 156 131 50 117 57 66 76 97 10 210 208 55 141 7 20 18 194 142 126 64 77 19 79 181 199 147 191 146 58 238 169 239 14 220 9 110 73 23 244 215 157 47 94 198 149 202 245 111 107 197 176 108 150 123 4 182 127 130 12 196 115 163 89 8 235 171 252 118 0 25 106 120 44 109 87 152 201 82 251 158 151 148 192 61 206 38 241 102 36 133 6 205 71 26 229 160 250 84 92 86 27 43 223 234 189 3 161 28 39 172 69 114 105 173 29 5 209 224 221 59 34 116 124 159 88 187 78 93 228 72 243 121 53 40 45 177 91 122 140 154 51 183 113 68 174 155 222 184 33 37 70 200 119 30 1 180 128 178 185 212 203 13 213 168 134 170 100 216
Next
Chapter Start
Skip to Next Chapter
Table of Contents
Main Page
Home Page