Quadibloc 23 is another cipher designed to achieve high security through many repetitions of a very simple round function.
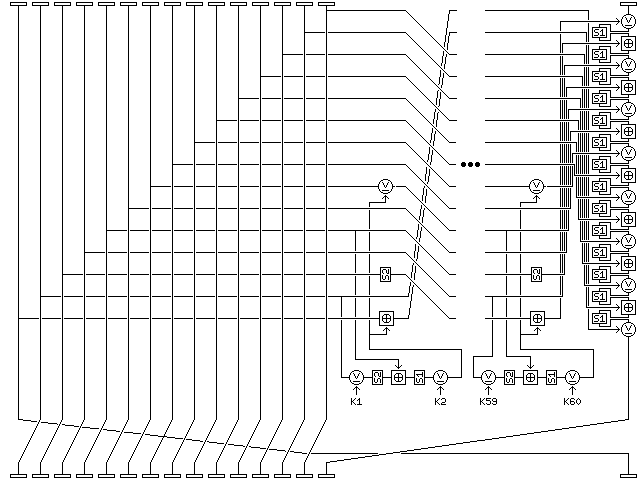
The basic Quadibloc 23 round, sixty-four of which make up the Quadibloc 23 block cipher, is shown below:

Quadibloc 23 is a cipher which acts on a 128-bit block, manipulated as a series of 16 bytes. In each round, the first 15 bytes are used as input into an f-function which itself consists of 30 rounds of a very simple type. The 15-byte output from those 30 rounds is then used to modify the rightmost byte.
A round within the f-function proceeds as follows:
The rounds within the f-function are very simple, similar to those in Treyfer. Thirty such rounds involve two passes through the entire 15 bytes of the input, and thus this is almost the minimal number of rounds required for thorough diffusion within the f-function.
Note that in successive rounds, what begins as the seventh byte of the block, which is XORed with the f-function output, then becomes the fifth byte, an f-function input, thus providing rapid diffusion, and then goes through S2, and finally has the f-function output added to it.
The second byte of the block is used as the other f-function input, leading to the use of an unrelated byte through which diffusion is delayed.
The overall round, which operates on the 16-byte block, and of which there are 64 in the cipher, consists of the following steps:
The fact that this 15-byte output is used to modify only one byte of the block, in a nonlinear fashion, slows diffusion through the cipher as a whole, but the fact that so much of the f-function output is, in a sense, discarded, even though all of the f-function output affects the substitution experienced by the rightmost byte, is what is believed to be the source of the strength of the cipher.
Sixty-four rounds amount to four passes through the entire block, which again is a minimal number. But the simple round within the f-function is performed 1,920 times within the block cipher.
Note that the first byte of the block becomes the first byte of the 15-byte f-function input; to show the f-function proceeding from the top down, except rotated 90 degrees, required reversing the bytes to apply the first byte of the output to the sixteenth byte first; thus, the byte reversal step on the right of the diagram is the result of artistic convention.
The key material required by the cipher consists of 3,840 one-byte subkeys and one key-dependent S-box with 256 8-bit entries.
Initially, the key-dependent S-box S2 is filled with the contents of S1.
Initially, the subkeys for the first round are the bytes of the key, repeated as necessary, and for the second round, the same, but starting with the second byte of the key, and so on. Keys for sixteen rounds are produced in this way. If the key is longer than 60 bytes in length, then it is split into two halves, and the first half is used to provide the keys for odd-numbered rounds, starting one byte later every two rounds, and the second half is used to provide the keys for even-numbered rounds, starting one byte later every two rounds.
A key may be from one to 60 bytes long, or from 62 to 120 bytes long and a multiple of two bytes in length.
Keys are produced by repeatedly performing a sixteen-round version of the cipher itself on the starting value
00 71 E2 53 C4 35 A6 17 88 F9 6A DB 4C BD 2E 9F
which can be formed as successive multiples of 71 hexadecimal, modulo 256.
The first thirty-two iterations of the key generating process produce alternately 16 bytes of subkeys or 16 bytes of data for use in constructing the S-box S2.
Then subsequent iterations always produce 16 bytes of subkey material; an additional two hundred and twenty-four iterations are required for this purpose.
The data for producing S-box S2 is used as follows: starting with the byte at position 0 in that buffer, and continuing to the byte in position 255, where the byte at position n has value m, the bytes at position n and m in a buffer originally containing a copy of S-box S1 are exchanged.
This design is an attempt to produce, with a design of extreme simplicity, but considerable slowness, a highly secure block cipher. The construct used as its main combiner is one that is inspired by rotor ciphers, and which I previously used in examples appearing in the next section, the one on stream ciphers.
Next
Start of Section
Skip to Next Chapter
Table of Contents
Main Page